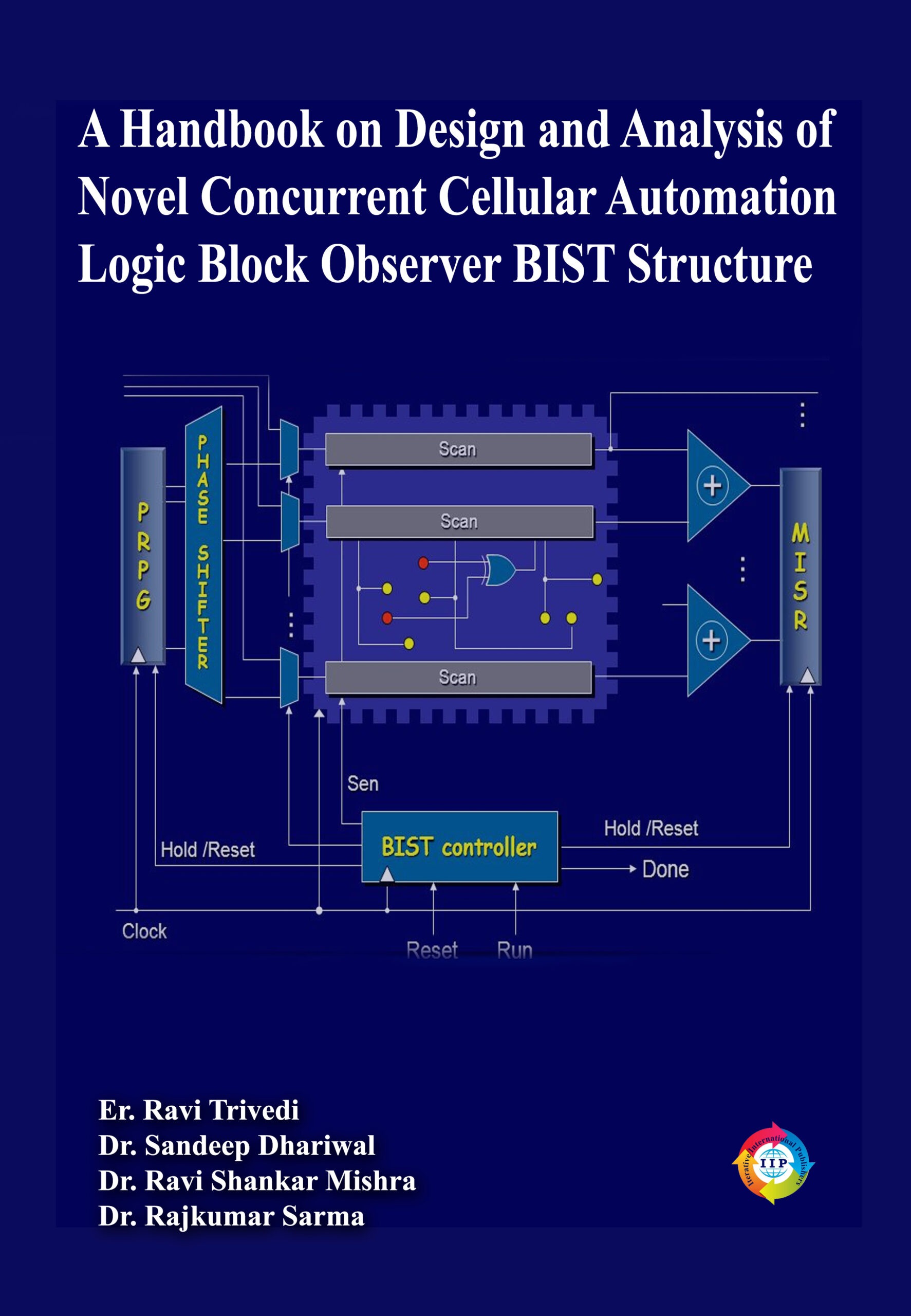
The Mobile Ad hoc Network (MANET) is a dynamic and self-configuring network composed of mobile nodes without the reliance on any established infrastructure. MANETs have gained significant attention due to their flexibility and potential applications in various fields such as military operations, disaster relief, and sensor networks. However, the absence of a centralized authority and the inherent vulnerability to security threats pose considerable challenges in ensuring the integrity and confidentiality of data transmission.
Among the multitude of security threats faced by MANETs, the presence of malicious nodes, particularly wormhole attacker nodes, presents a significant concern. Wormhole attacks involve the creation of a tunnel between two distant points in the network, allowing an attacker to intercept and manipulate communication packets. This clandestine activity can disrupt network operations, compromise sensitive information, and undermine trust among network participants.
In response to this critical security challenge, this book aims to provide a comprehensive exploration of techniques and strategies for the elimination of wormhole attacker nodes in MANETs. By delving into the underlying principles of MANETs and the intricacies of wormhole attacks, this book endeavors to equip readers with a profound understanding of the threat landscape and the importance of robust security measures.









Reviews
There are no reviews yet.